This section demonstrates how to secure the Tomcat Manager Application by enabling access via TLS/SSL Encryption.
If you do not intend to use the Tomcat Manager Application, you can skip this section and proceed to removing unused web applications.
Rationale
The Tomcat The Manager application:
- “Free” web application that comes with Tomcat distribution that lives in the Tomcat Lives in the
${tomcat_home}/webapps/managerdirectory. - Not enabled by default.
- Allows Tomcat administrators to deploy, un-deploy, or reload web applications such as the TDS without having to shut down and restart Tomcat.
- If exploited, an attacker can use the Manager application to install programs on your server willy-nilly.
- If you choose to enable the Manager application, we highly recommend enabling digested passwords and TLS/SSL encryption for the Manager application.
- Restricting access to the Manager application to a small subset of IP addresses or host names using a Tomcat valve is also a good idea.
- Uninstall this application if you don’t plan to use it.
Enabling TLS/SSL For The Tomcat Manager Application
The following example demonstrates enabling TLS/SSL for the Tomcat Manager Application on a linux system as the root user.
-
Modify the deployment descriptor (
${tomcat_home}/webapps/manager/WEB-INF/web.xml)of the Tomcat Manager application.Use your favorite editor to open the deployment descriptor for the Tomcat Manager application:
# vi ${tomcat_home}/webapps/manager/WEB-INF/web.xmlLocate the
<security-constraint>elements (around line ~122):<!-- Define a Security Constraint on this Application --> <!-- NOTE: None of these roles are present in the default users file --> <security-constraint> <web-resource-collection> <web-resource-name>HTML Manager interface (for humans)</web-resource-name> <url-pattern>/html/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-gui</role-name> </auth-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>Text Manager interface (for scripts)</web-resource-name> <url-pattern>/text/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-script</role-name> </auth-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>JMX Proxy interface</web-resource-name> <url-pattern>/jmxproxy/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-jmx</role-name> </auth-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>Status interface</web-resource-name> <url-pattern>/status/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-gui</role-name> <role-name>manager-script</role-name> <role-name>manager-jmx</role-name> <role-name>manager-status</role-name> </auth-constraint> </security-constraint>The Tomcat 8.x version of the Manager application deployment descriptor contains a
<security-constraint>section for each of the four possibleContactPaths(as per Manager Application section of the Tomcat Migration Guide).Add a
<user-data-constraint>with a<transport-guarantee>ofCONFIDENTIALfor the desiredContactPathsto to enable port-forwarding to port8443:<!-- Define a Security Constraint on this Application --> <!-- NOTE: None of these roles are present in the default users file --> <security-constraint> <web-resource-collection> <web-resource-name>HTML Manager interface (for humans)</web-resource-name> <url-pattern>/html/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-gui</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>Text Manager interface (for scripts)</web-resource-name> <url-pattern>/text/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-script</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>JMX Proxy interface</web-resource-name> <url-pattern>/jmxproxy/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-jmx</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> <security-constraint> <web-resource-collection> <web-resource-name>Status interface</web-resource-name> <url-pattern>/status/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>manager-gui</role-name> <role-name>manager-script</role-name> <role-name>manager-jmx</role-name> <role-name>manager-status</role-name> </auth-constraint> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint> -
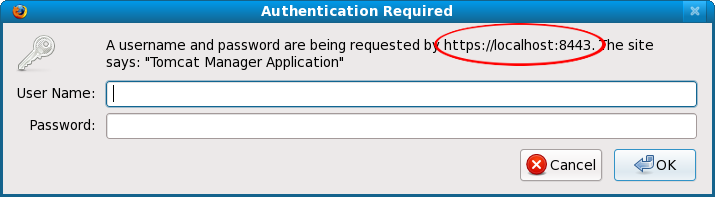
Verify TLS/SSL has been enabled for the Tomcat Manager application.
Restart Tomcat and verify TLS/SSL has been enabled for the Tomcat Manager application: http://localhost:8080/manager/html/
 Important: You will have to perform this configuration change to the Manager application deployment descriptor every time you upgrade Tomcat. :-|
Important: You will have to perform this configuration change to the Manager application deployment descriptor every time you upgrade Tomcat. :-|
Troubleshooting
- Check the XML syntax in
${tomcat_home}/webapps/manager/WEB-INF/web.xmlto make sure it is well-formed and without error. - Did you specify a
<transport-guarantee>ofCONFIDENTIAL? - Did you restart Tomcat after you made your changes to
web.xml?
Resources
- Manager App HOW-TO The Apache Tomcat document referencing how to use and configure the Manager application.
- Tomcat Migration Guide A document detailing the various changes between Tomcat versions contains a section dedicated to the Manager application.